Category: Cybersecurity
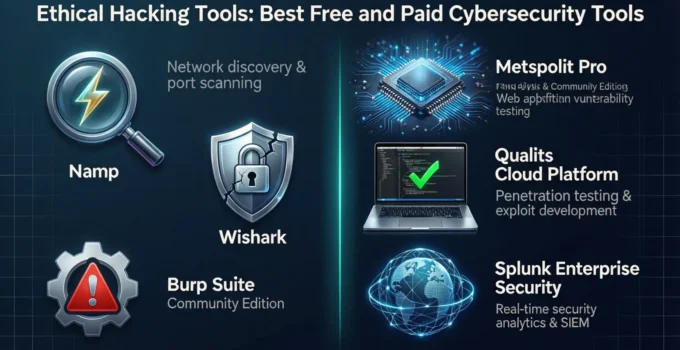
Introduction Hacking tools—also known as ethical hacking tools, penetration testing tools, or cybersecurity testing tools—are designed to help security professionals identify system weaknesses before cybercriminals exploit them. While the phrase …
Introduction Modern businesses face constant digital risks, making a strong Security Firewall essential for safe online operations. A well-designed Security Firewall supports cybersecurity by enabling network protection, threat detection, …
Introduction Internet of Things in Cybersecurity represents the critical practice of protecting interconnected devices, their data, and the networks they operate on from evolving cyber threats. As projections estimate …
Introduction In an era where digital systems underpin every facet of modern life, the term “Ethical Hacking” often evokes confusion. At its core, Ethical Hacking is a sanctioned, defensive cybersecurity practice where …
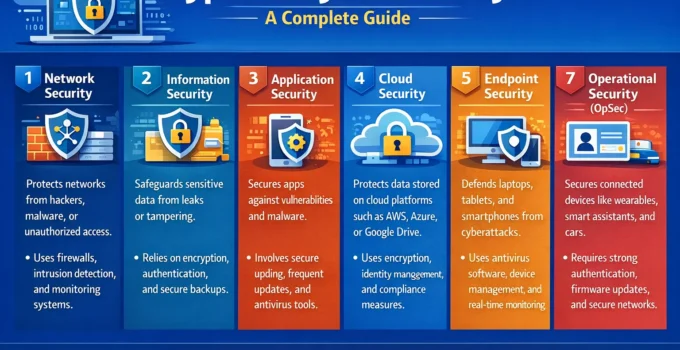
Introduction In today’s digital age, understanding the different Types of Cybersecurity is essential for protecting data, networks, and systems from ever-growing threats. In today’s digital landscape, understanding the distinct …
Introduction The convergence of Artificial Intelligence and Cybersecurity is defining a new era of digital risk and resilience. No longer a speculative future trend, it is the present reality, …
Introduction In today’s digital age, understanding Online Cyber Threats is more important than ever. From phishing scams to ransomware, the rise of cybercrime makes Online Cyber Threats a top priority …
Introduction As humanity pushes further into the cosmos, Cybersecurity in Space has become a critical concern. Satellites, space stations, and communication systems are increasingly vulnerable to digital threats, making …
Introduction The digital battlefield is rapidly evolving, and AI vs Hackers is at the center of it. As cyberattacks grow more advanced, traditional security tools struggle to keep up. …